Ansible with its huge community and broad platform support is one of the tools you should have a look at to address your cloud automation demands.
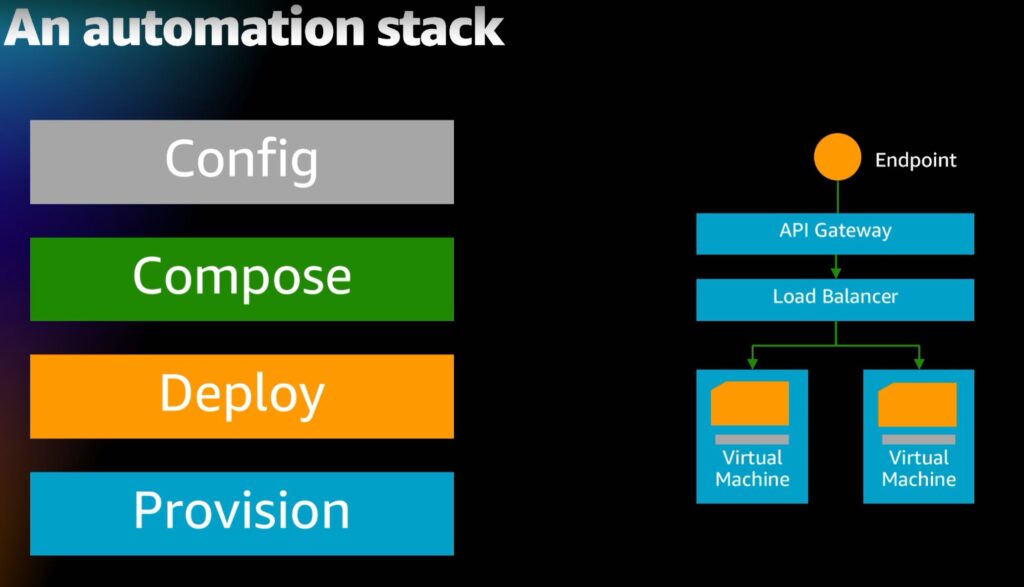
Azure Automation with Ansible can address all layers of the automation stack introduced by Gregor Hohpe in his AWS Innovate Keynote Talk. But it would be best if you decided for yourself whether it is the best tool for all these challenges.
Development Machine
I created a new Development Machine for my first steps in Azure Automation with Ansible and chose Ubuntu as the Guest OS. Of course, an Azure virtual machine was the best choice here.
Install Ansible
Installing Ansible on Ubuntu is straightforward using the PPA.
|
|
Installing Ansible Azure Collection
I recommend installing the Azure.Azcollection from the Ansible Galaxy.
|
|

Install dependencies for the collection
To avoid incompatibility install the dependencies required by the collection with the requirements-file shipped with the Azure.Azcollection.
|
|
Storing Azure credentials
On my development machines, I prefer storing the credentials in a password file. For CI/CD Pipelines or environments like Ansible Automation Platform, environment variables are the way to go (will be covered later).
Using the Azure Resource Manager modules requires authenticating with the Azure API. You can choose from two authentication strategies:
-
Active Directory Username/Password
-
Service Principal Credentials
I chose Service Principal Credentials.
Create Service Principal:
|
|
Store Credentials:
|
|
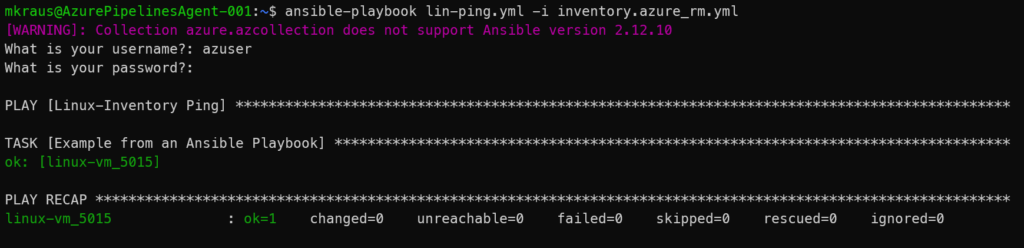
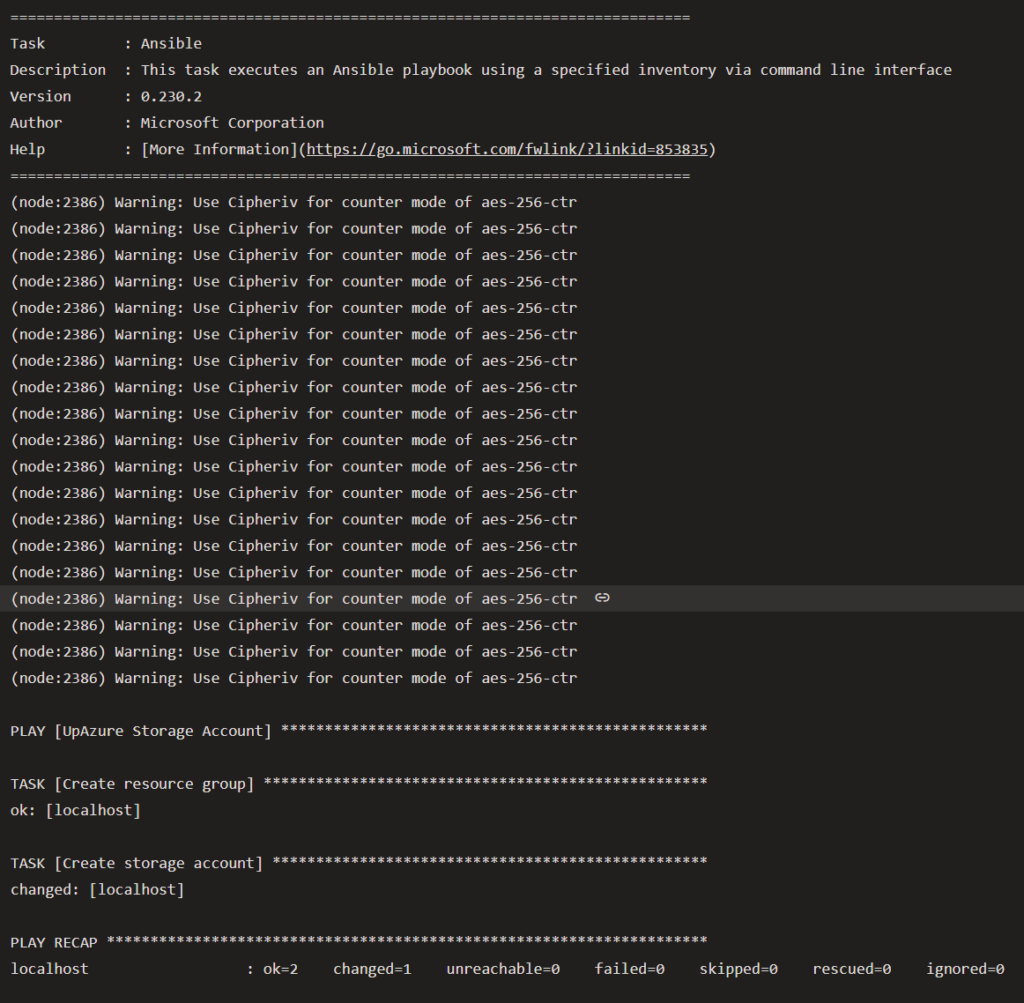
Run the first playbook
To test the newly created setup, I run a simple playbook that creates an empty Azure Resource Group.
|
|
|
|


Ansible dynamic inventories
Using dynamic inventories of your Azure resources using Ansible opens up a whole new range of areas of application and possibilities for Azure Automation with Ansible. The underlying idea is to create Ansible inventory groups based on the Azure configuration (e.g. Dependency) and the attributes of the resources (e.g. Tags). Playbooks can be started against these groups.
To use the inventory, create a configuration based on the Azure dynamic-inventory plug-in.
|
|
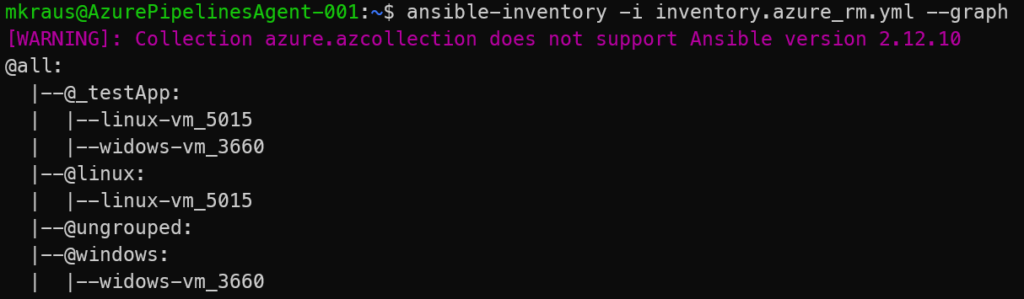
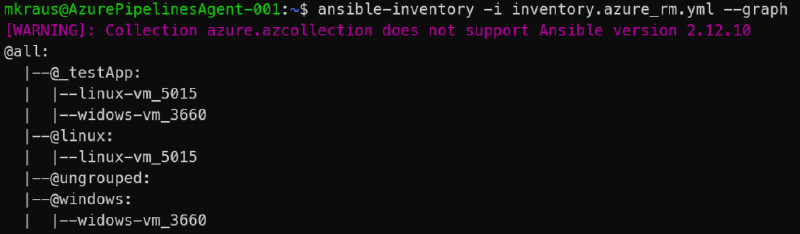
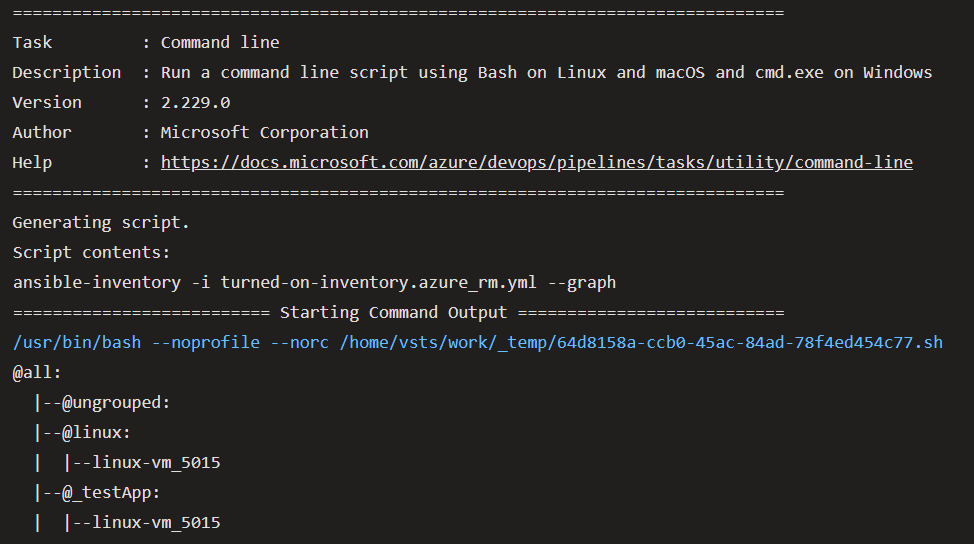
In this example, you can see the empty default group “ungrouped”, because all running Azure VMs are grouped. Two conditional groups (Windows and Linux) are created based on the Guest OS, derived from different attributes. Both running Azure have the same tag “application:testApp” and therefore are members of the same keyed group. Keyed groups are mighty and flexible because you don’t need to know all the future Application Tags, as new applications are created a new group is created in the dynamic inventory,
To see all attributes of your inventory objects, use the --list parameter.
|
|
Using the inventory
You can reference all groups of the dynamic inventory like other Ansible Hosts.
|
|
Azure DevOps Pipeline
Azure DevOps is a great platform for managing or consuming your cloud platform through IaC. Azure DevOps Pipelines offer a secure environment to apply your Ansible playbooks.
Credential handover
As mentioned earlier in this post, for CI/CD pipelines, environment variables are the preferred way to hand over the credentials. I decided to use a variable group that is imported into the pipeline.
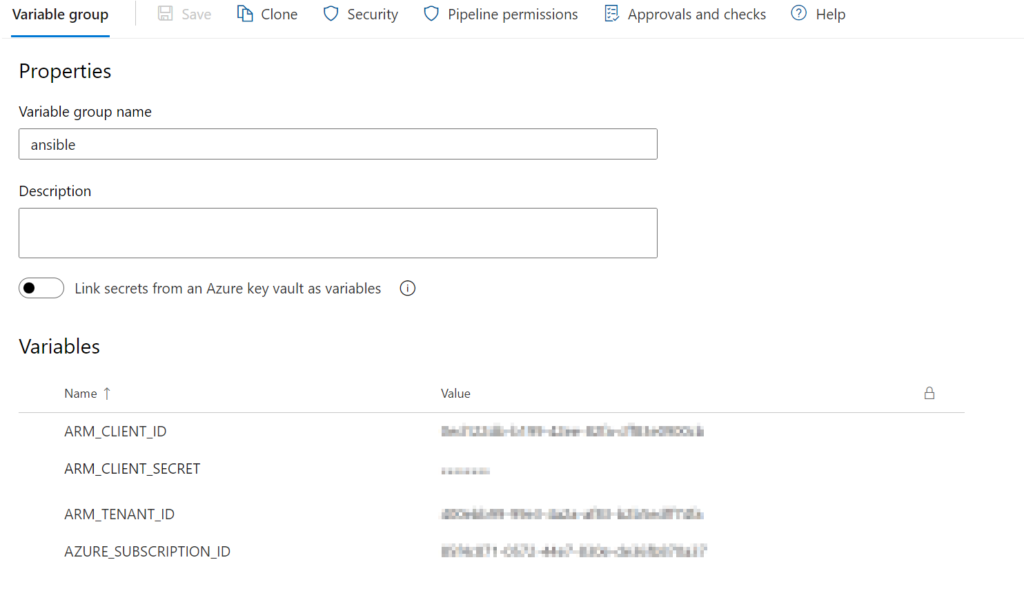
|
|
Ansible extension
Azure Pipeline capabilities can be extended with additional (third party) extensions. For Azure Automation with Ansible, the Ansible extension from the Marketplace is required.
This extension includes a build/release task to integrate with Ansible. The task executes a given Ansible playbook on a specified list of inventory nodes via command line interface.
Pipeline with Microsoft Hosted Agents
With Microsoft Hosted Agents you have minimal effort in operations and maintenance. Each time you run a pipeline, you get a fresh virtual machine for all Tasks within the pipeline. Microsoft takes care of the updates of the image.
| Image | Classic Editor Agent Specification | YAML VM Image Label | Included Software |
|---|---|---|---|
| Windows Server 2022 with Visual Studio 2022 | windows-2022 | windows-latest OR windows-2022 |
Link |
| Windows Server 2019 with Visual Studio 2019 | windows-2019 | windows-2019 |
Link |
| Ubuntu 22.04 | ubuntu-22.04 | ubuntu-latest OR ubuntu-22.04 |
Link |
| Ubuntu 20.04 | ubuntu-20.04 | ubuntu-20.04 |
Link |
| macOS 13 Ventura | macOS-13 | macOS-13 |
Link |
| macOS 12 Monterey | macOS-12 | macOS-latest OR macOS-12 |
Link |
| macOS 11 Big Sur | macOS-11 | macOS-11 |
Link |
Reference: Microsoft-hosted agents
Pipeline definition
|
|
Pipeline execution
What is prepared for the actual execution?
-
Install the latest Ansible version (runner-image Ansible version is too old)
-
Install Ansible Azure Collection
-
Install all requirements of the Ansible Azure Collection
Pipeline with Self Hosted Agents
Unfortunately, there are also disadvantages to using pipelines with Microsoft Hosted Agents. The fact that each run uses a new image has a great disadvantage if you need many of your tools not included in the runner-image (or newer versions) in the execution environment. Installing the requirements of the Ansible Azure Collection takes at least 70 seconds. With a Self Hosted Agent, you can persistently prepare your execution environment.
Agent preparation
The Ubuntu Azure VM I use was prepared similarly to the Development Machine in the first chapter, plus the Agent Package. Please check the detailed instructions for additional information.
After the manual run or the service-start, the agent initiates an SSL connection to your Azure DevOps project, destinations are listed in the FAQ of the detailed instructions.
|
|

Pipeline definition
|
|