Within a past project I was working on a topic that was covered by Daniel Paluszek in his blog post Security Compliance – Pre-configure your vApp firewall rules inside vCloud Director using NSX DFW (Part 1 of 2). But I had slightly different goals than Daniel, I had the premise to represent the whole configuration inside the vCloud Director user interface and the naming of the virtual machines was needed to be flexible. So to the concept of Dynamic Security Group with Tag was born. VMware NSX Security Groups and Security Tags can also be used in vCloud Director multi tenancy environments.
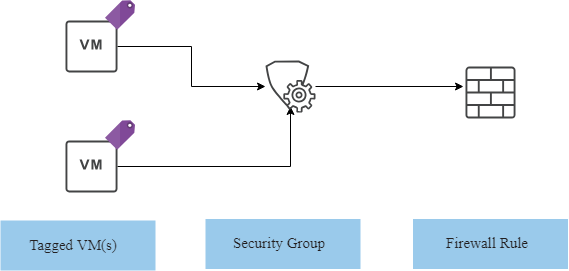
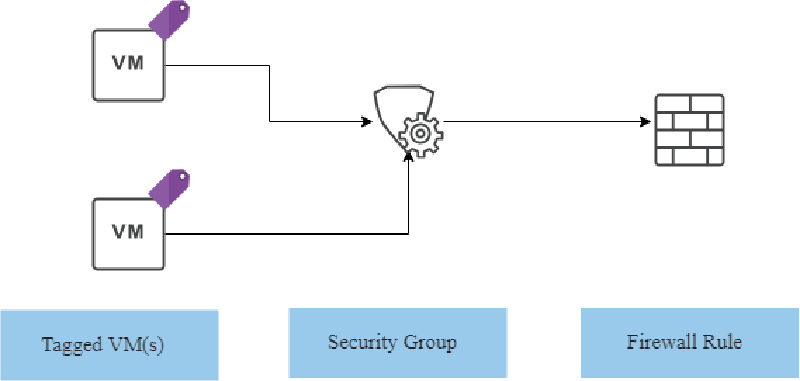
The core of the concept coveres:
- An App specific, static NSX DFW rule
- A Security Group, which is source or destination in the NSX Distributed Firewall (DFW) rule
- A Security Tag, which is the membership criteria of the Security Group
At the end, new firewall rules are applied to a VM by adding a Security Tag. This can be done very fast via the API, or my updated PowerShell Module for the vCloud Director API for NSX (Older Blog Post: PowerShell Module for vCloud Director NSX API).
Dynamic Security Group with Tag
I will cover all of the objects related to this concept. The UI used in my examples is the vCloud Director HTML5 View of the OrgVDC Distributed Firewall (DFW). All of the objects and configuration can also be viewed with my PowerShell Module. In addition, the Module can be used to manage the Tag assignment of the VMs.
Security Tag
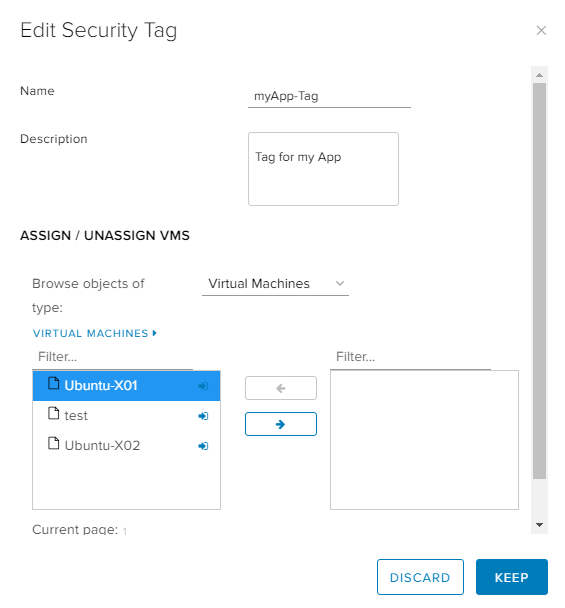
The first component of this concept is the Security Tag. The Tag will be applied to the VM(s) that should be part of Security Group.
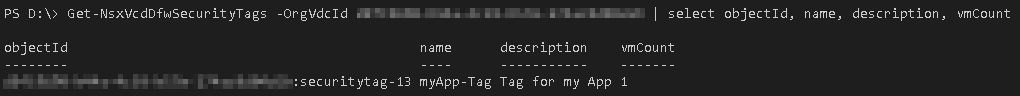
All Security Tags of the OrgVDC via PowerShell:
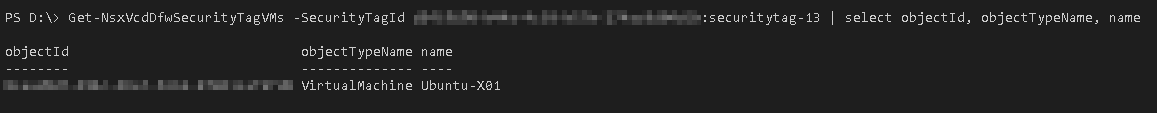
VMs with a known Security Tag can be shown with the Get-NsxVcdDfwSecurityTagVMs function:
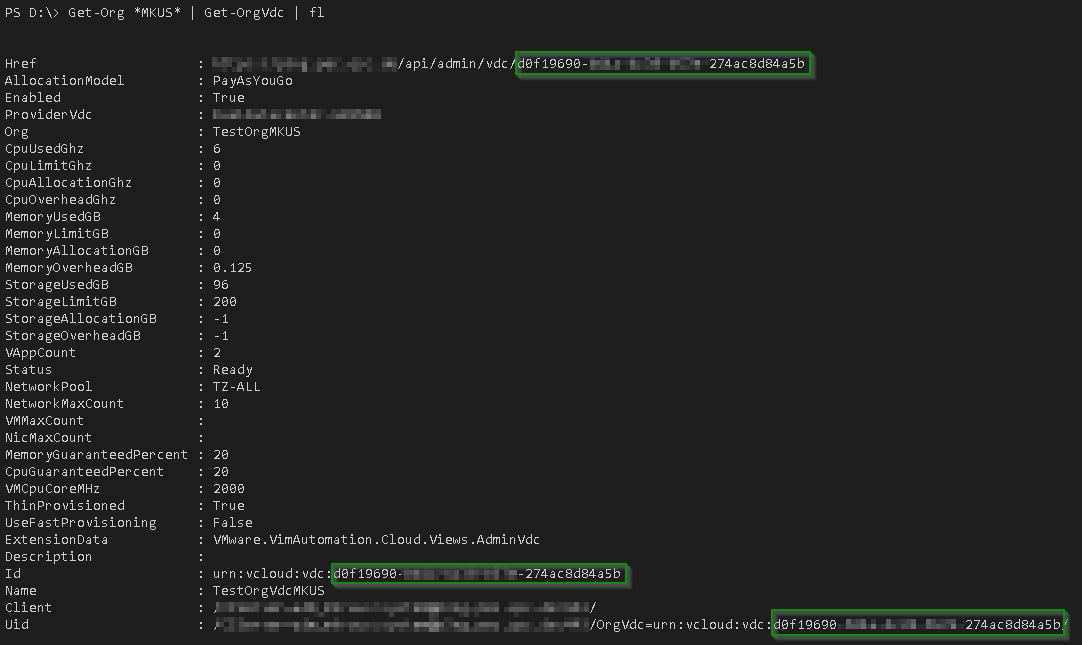
Get the OrgVDC ID
The Get-NsxVcdDfwSecurityTags function needs the ID of the OrgVDC as input. In most cases I use the PowerCLI to gather such details:
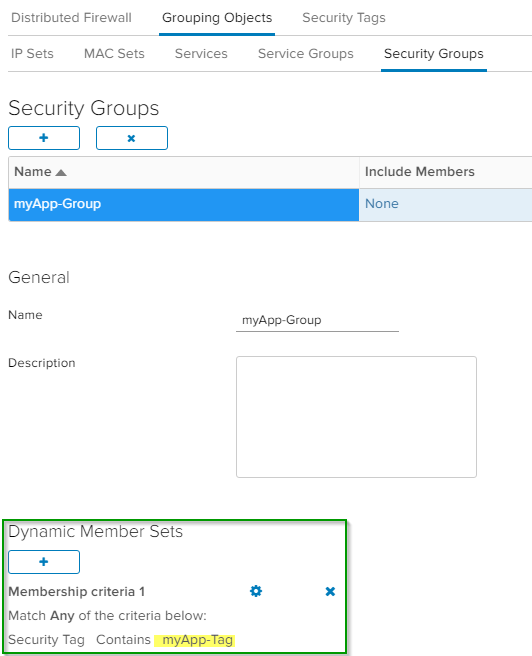
Security Group
NSX Security Groups can be configured with static memberships or dynamic memberships with different criterias. One possible criteria is a Security Tag.
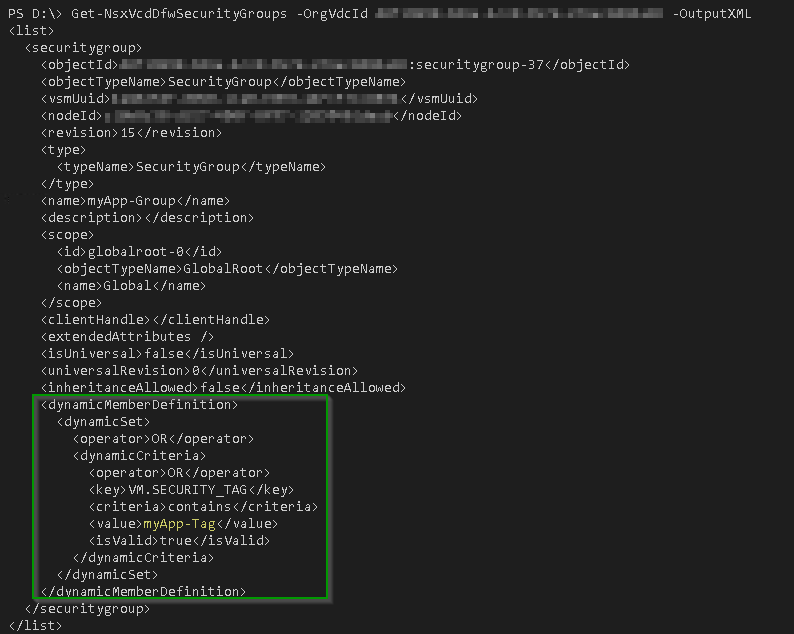
The API also shows the Dynamic Security Group membership with the Security Tag as criteria:
Distributed Firewall Rule Rule
The Distributed Firewall Rule contains the Dynamic Security Group with Tag as Source or Destination, depending on your concept.
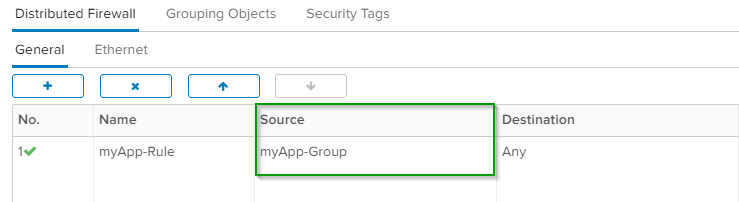
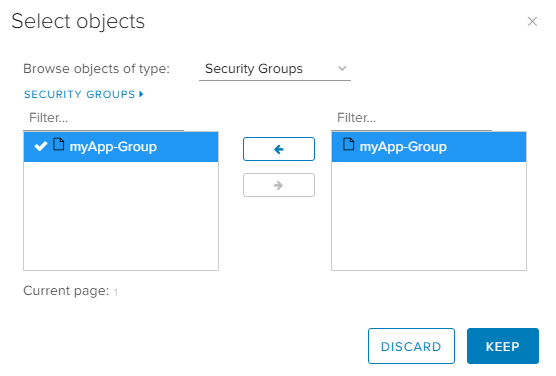
The selected Source is a custom Security Group:
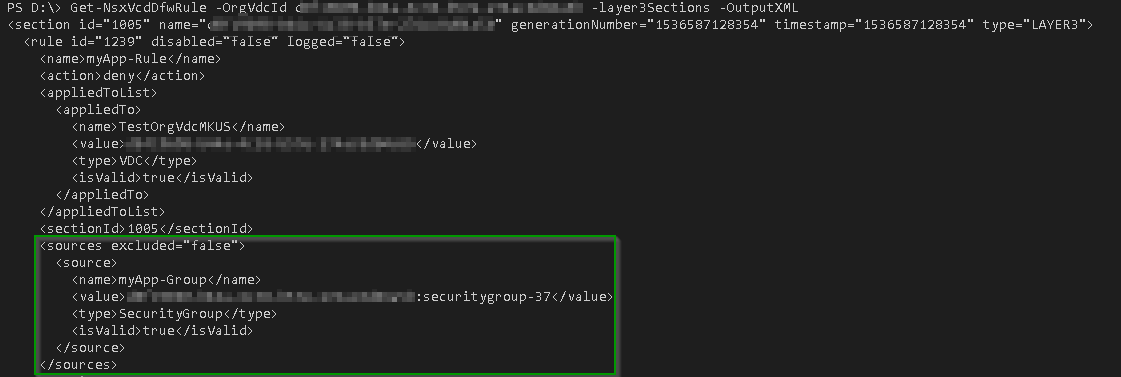
The DFW Rules in vCloud Director can also be reported from the API with my PowerShell Module:
Tagging of VMs
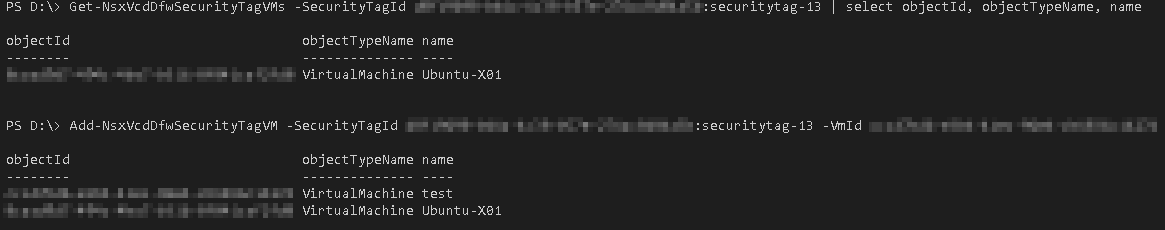
The next step is adding and removing the Security Tag. This can be done via the vCloud Director UI or with the functions Add-NsxVcdDfwSecurityTagVM and Remove-NsxVcdDfwSecurityTagVM.
Get Tagged VMs / Add Tag to a VM:
Remove Tag from a VM:

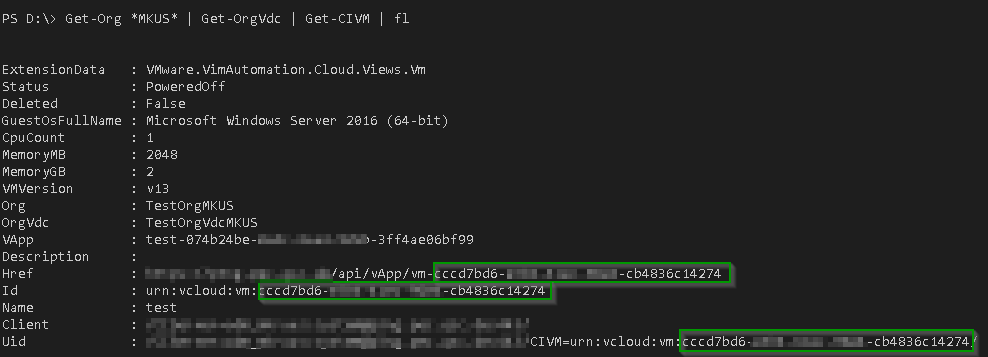
Get the VM ID
The required VM ID can also be gathered with PowerCLI:
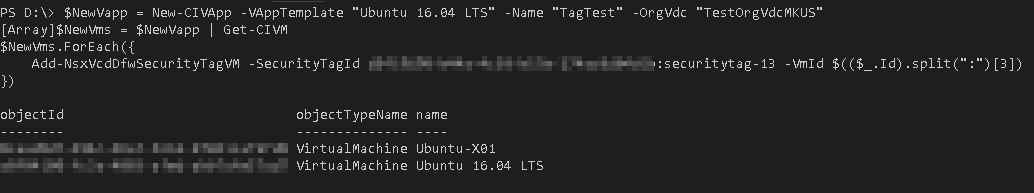
Provision VM with Security Tag
The benefit of this concept becomes clear by the fact that with only three additional lines (one if you do without good legibility) of PowerShell code the whole DFW Ruleset can be applied to a newly provisioned VM.
|
|