There are already a lot of great projects out there for the Veeam unattended installation. One of the most advanced projects is for sure the Chef cookbook for Veeam Backup and Replication. I myself have also already worked on that topic, and have done some rework of the PowerShell script from Timothy Dewin. The Veeam unattended installation with Ansible is the next evolution of my prior project (Veeam unattended installation with PowerShell)and the first step for further Veeam integration into Ansible.
The Ansible Playbook I have created will install a Veeam Backup & Replication Server 9.5 Update 4a on an unprepared Windows Server (in my case Winddows Server 2019). The Veeam unattended installation with Ansible will install all pre-requirements, the SQL Server Express, the Veeam Backup Catalog, the Veeam Backup & Replication Server, the Veeam Backup & Replication Console and all Veeam Explorers.
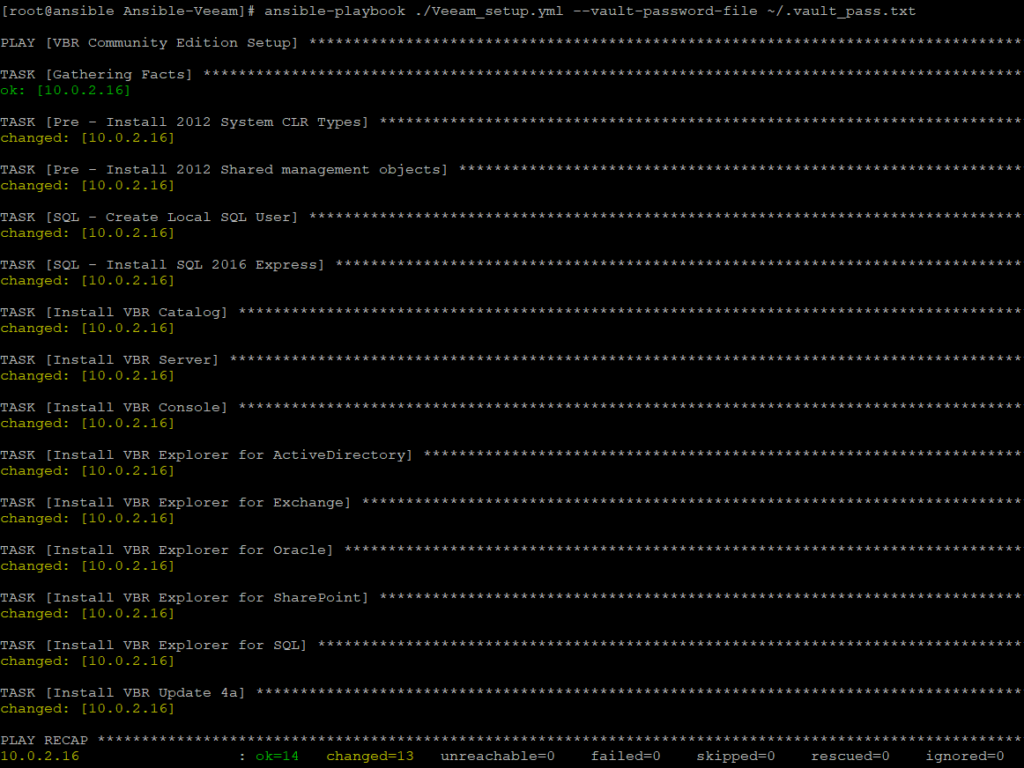
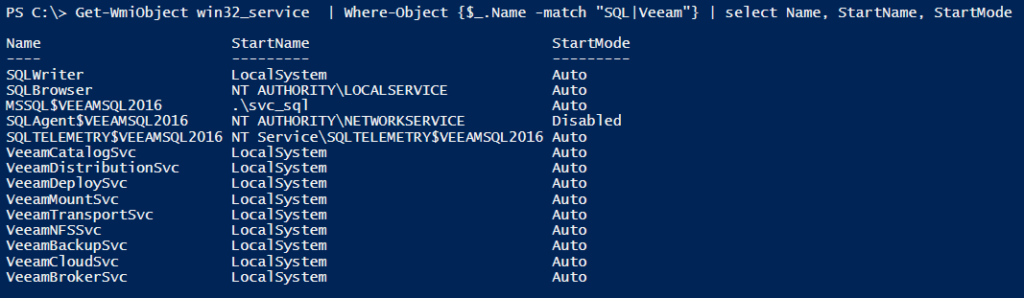
A special requirement I have tried to achieve was the use of SQL authentication to the Veeam Database. If SQL authentication is used, all the Veeam services can run in the “Local System” context. The SQL service should be started with normal user privileges Side-by-Side on the Veeam Backup & Replication Server.
Veeam unattended installation
After the user creation, the pre-requirements installation and the SQL Server setup the following installation order needs to be done for the basic Veeam Backup & Replication Server setup:
- Veeam Backup Catalog
- Veeam Backup & Replication Server
- Veeam Backup & Replication Console
- Veeam Explorers:
- Veeam Explorer for Active Directory
- Veeam Explorer for Exchange
- Veeam Explorer for Oracle
- Veeam Explorer for SharePoint
- Veeam Explorer for Microsoft SQL
- Veeam Update 4a
The Veeam Backup Enterprise Manager and the Veeam Cloud Connect Portal are currently not installed yet.
Ansible preperation
In addition to the Ansible Development environment, I have already used for a few other projects, an additional windows server needs to be managed by Ansible (the Veeam Backup & Replication Server).
Unlike Linux/Unix hosts, which use SSH by default, Windows hosts are configured with WinRM for the Ansible access (Windows Remote Management). With WinRM there are several different options that can be used when authenticating with an account.
| Option |
Local Accounts |
Active Directory Accounts |
Credential Delegation |
HTTP Encryption |
| Basic |
Yes |
No |
No |
No |
| Certificate |
Yes |
No |
No |
No |
| Kerberos |
No |
Yes |
Yes |
Yes |
| NTLM |
Yes |
Yes |
No |
Yes |
| CredSSP |
Yes |
Yes |
Yes |
Yes |
I have choosen NTLM with HTTP Encryption (set in group_vars):
1
2
3
4
5
6
7
8
|
---
ansible_user: Administrator
ansible_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
ansible_port: 5986
ansible_connection: winrm
ansible_winrm_transport: ntlm
ansible_winrm_server_cert_validation: ignore
|
For the Windows Server preparation to grant WinRM access, I have used the ConfigureRemotingForAnsible.ps1 PowerShell script.
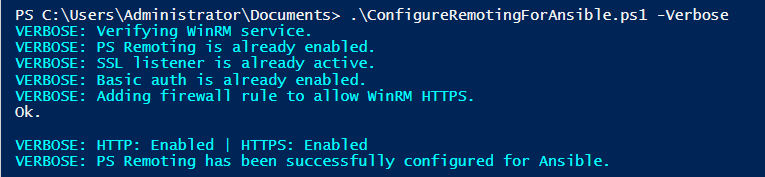
The Ansible Host requires an additional WinRM Python client (pywinrm) for the WinRM management with NTLM authentication:
Note:
If you want to use Kerberos or CredSSP, please check the Windows Remote Management Documentation for the list of additional packages and configurations.
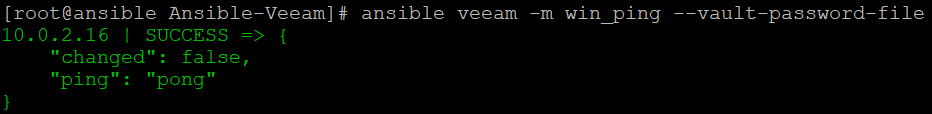
To verify the access to the Windows box, a simple win_ping task can be executed against the “veeam” inventory group:
Ansible Playbook
The playbook itself includes all required variables for the setup and is executed against an inventory Host Group called “veeam”. This group includes in my case only one Server.
To handle all required installation steps, the win_package Ansible module is used by the playbook. This Ansible module automatically handles most of the required escaping for the arguments but needs a special syntax for complex scenarios (See also: Passing arguments for win_package module).
In a real-world scenario, an additional task for the installation media mount might be added to the playbook. For example my mounting a datastore image with the vmware_guest module.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
|
- name: VBR Community Edition Setup
hosts: veeam
gather_facts: yes
vars:
vbr_source: "D:\\"
sql_username: "svc_sql"
sql_userpassword: !vault |
$ANSIBLE_VAULT;1.1;AES256
sql_sapassword: !vault |
$ANSIBLE_VAULT;1.1;AES256
tasks:
- name: Pre - Install 2012 System CLR Types
win_package:
path: "{{ vbr_source }}Redistr\\x64\\SQLSysClrTypes.msi"
state: present
tags: pre
- name: Pre - Install 2012 Shared management objects
win_package:
path: "{{ vbr_source }}Redistr\\x64\\SharedManagementObjects.msi"
state: present
tags: pre
- name: SQL - Create Local SQL User
win_user:
name: "{{ sql_username }}"
password: "{{ sql_userpassword }}"
password_never_expires: yes
state: present
groups:
- Users
tags: pre
- name: SQL - Install SQL 2016 Express
win_package:
path: "{{ vbr_source }}Redistr\\x64\\SqlExpress\\2016SP1\\SQLEXPR_x64_ENU.exe"
product_id: SQL 2016 Express
arguments:
- '/q'
- '/ACTION=Install'
- '/IACCEPTSQLSERVERLICENSETERMS'
- '/FEATURES=SQL'
- '/INSTANCENAME=VEEAMSQL2016'
- '/SQLSVCACCOUNT={{ sql_username }}'
- '/SQLSVCPASSWORD={{ sql_userpassword }}'
- '/SECURITYMODE=SQL'
- '/SAPWD={{ sql_sapassword }}'
- '/ADDCURRENTUSERASSQLADMIN'
- '/UPDATEENABLED=0'
- '/TCPENABLED=1'
- '/NPENABLED=1'
tags: sql
- name: Install VBR Catalog
win_package:
path: "{{ vbr_source }}Catalog\\VeeamBackupCatalog64.msi"
state: present
arguments:
- 'VBRC_SERVICE_ACCOUNT_TYPE=1'
- 'ACCEPT_THIRDPARTY_LICENSES=1'
tags: vbr
- name: Install VBR Server
win_package:
path: "{{ vbr_source }}Backup\\Server.x64.msi"
state: present
arguments: "VBR_SERVICE_ACCOUNT_TYPE=1 VBR_SQLSERVER_AUTHENTICATION=1 VBR_SQLSERVER_SERVER=(local)\\VEEAMSQL2016 VBR_SQLSERVER_USERNAME=sa VBR_SQLSERVER_PASSWORD={{ sql_sapassword }} ACCEPT_THIRDPARTY_LICENSES=1 ACCEPTEULA=YES"
tags: vbr
- name: Install VBR Console
win_package:
path: "{{ vbr_source }}Backup\\Shell.x64.msi"
state: present
arguments:
- 'ACCEPTEULA=YES'
- 'ACCEPT_THIRDPARTY_LICENSES=1'
tags: vbr
- name: Install VBR Explorer for ActiveDirectory
win_package:
path: "{{ vbr_source }}Explorers\\VeeamExplorerForActiveDirectory.msi"
state: present
arguments:
- 'ACCEPT_EULA=1'
- 'ACCEPT_THIRDPARTY_LICENSES=1'
tags: vbr
- name: Install VBR Explorer for Exchange
win_package:
path: "{{ vbr_source }}Explorers\\VeeamExplorerForExchange.msi"
state: present
arguments:
- 'ACCEPT_EULA=1'
- 'ACCEPT_THIRDPARTY_LICENSES=1'
tags: vbr
- name: Install VBR Explorer for Oracle
win_package:
path: "{{ vbr_source }}Explorers\\VeeamExplorerForOracle.msi"
state: present
arguments:
- 'ACCEPT_EULA=1'
- 'ACCEPT_THIRDPARTY_LICENSES=1'
tags: vbr
- name: Install VBR Explorer for SharePoint
win_package:
path: "{{ vbr_source }}Explorers\\VeeamExplorerForSharePoint.msi"
state: present
arguments:
- 'ACCEPT_EULA=1'
- 'ACCEPT_THIRDPARTY_LICENSES=1'
tags: vbr
- name: Install VBR Explorer for SQL
win_package:
path: "{{ vbr_source }}Explorers\\VeeamExplorerForSQL.msi"
state: present
arguments:
- 'ACCEPT_EULA=1'
- 'ACCEPT_THIRDPARTY_LICENSES=1'
tags: vbr
- name: Install VBR Update 4a
win_package:
path: "{{ vbr_source }}Updates\\veeam_backup_9.5.4.2753.update4a_setup.exe"
product_id: VBR Update 4a
arguments: "/silent /noreboot VBR_AUTO_UPGRADE=1"
tags: update
|
Latest version on GitHub: Veeam_setup.yml




