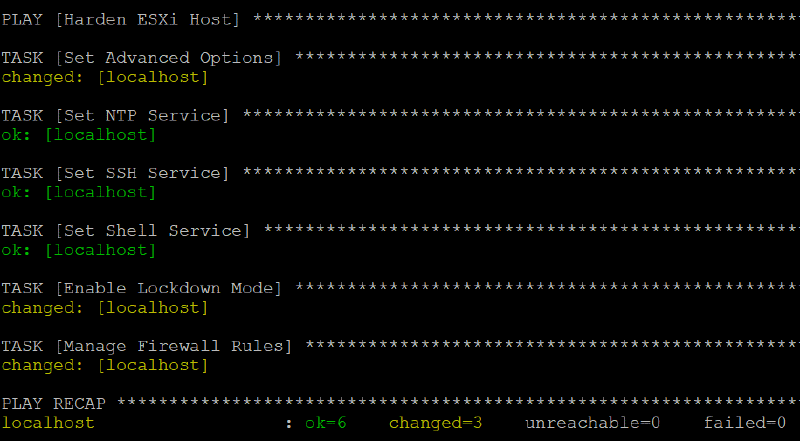
If you read the vSphere 6.7 Update 1 Security Configuration Guide you will agree that the security configuration of VMware ESXi hosts is mostly about managing services, advanced options, firewall rules, and lockdown mode. The Ansible Community has created all the modules required to do the VMware ESXi Security Configuration with Ansible.
This blog post is based on the environment created within a prior article: My Ansible Development Setup
ESXi Security Configuration Tasks
I have chosen most of the ESXi configuration options from the vSphere 6.7 Update 1 Security Configuration Guide and created a Playbook to enforce the VMware ESXi Security Configuration with Ansible.
Set Advanced Options
VMware ESXi advanced options can be modified with the Ansible vmware_host_config_manager module.
Warning:
Please be aware of this GitHub Issue: Inconsistent results with vmware_host_config_manager
The solution is also described later in this article.
| Option | Value |
| UserVars.ESXiShellInteractiveTimeOut | 900 |
| UserVars.ESXiShellTimeOut | 900 |
| UserVars.DcuiTimeOut | 600 |
| UserVars.SuppressShellWarning | 0 |
| Security.AccountLockFailures | 3 |
| Security.AccountUnlockTime | 900 |
| Security.PasswordQualityControl | similar=deny retry=3 min=disabled,disabled,disabled,disabled,15 |
| DCUI.Access | root |
| Net.BlockGuestBPDU | 1 |
| Config.HostAgent.plugins.solo.enableMob | false |
Ansible Code Snippet:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
- name: Set Advanced Options
vmware_host_config_manager:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
options:
"UserVars.ESXiShellInteractiveTimeOut": 900
"UserVars.ESXiShellTimeOut": 900
"UserVars.DcuiTimeOut": 600
"UserVars.SuppressShellWarning": 0
"Security.AccountLockFailures": 3
"Security.AccountUnlockTime": 900
"Security.PasswordQualityControl": "similar=deny retry=3 min=disabled,disabled,disabled,disabled,15"
"DCUI.Access": "root"
"Net.BlockGuestBPDU": 1
"Config.HostAgent.plugins.solo.enableMob": false
|
Manage Services
The vmware_host_service_manager module can be used to manage (start, stop, restart) services on VMware ESXi hosts.
| Service | State |
| NTPD | On |
| TSM-SSH | Off |
| TSM | Off |
Ansible Code Snippet:
1
2
3
4
5
6
7
8
9
10
|
- name: Set NTP Service
vmware_host_service_manager:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
service_name: ntpd
state: present
service_policy: on
|
Enable Lockdown Mode
The vmware_host_lockdown module can be used to manage administrator permission for the local administrative account when the VMware ESXi host is managed by a vCenter Server.
Ansible Code Snippet:
1
2
3
4
5
6
7
8
|
- name: Enable Lockdown Mode
vmware_host_lockdown:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
state: present
|
Manage Firewall Rules
The firewall configuration of a VMware ESXi host can be managed by the vmware_host_firewall_manager Ansible module.
| Rule | State |
| DHCP | Disabled |
| DHCPv6 | Disabled |
| SNMP | Disabled |
| iSCSI | Disabled |
Ansible Code Snippet:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
- name: Manage Firewall Rules
vmware_host_firewall_manager:
hostname: '{{ vcenter_hostname }}'
username: '{{ vcenter_username }}'
password: '{{ vcenter_password }}'
cluster_name: "{{ cluster_name }}"
validate_certs: no
rules:
- name: dhcp
enabled: False
- name: DHCPv6
enabled: False
- name: iSCSI
enabled: False
- name: snmp
enabled: False
|
Ansible Playbook
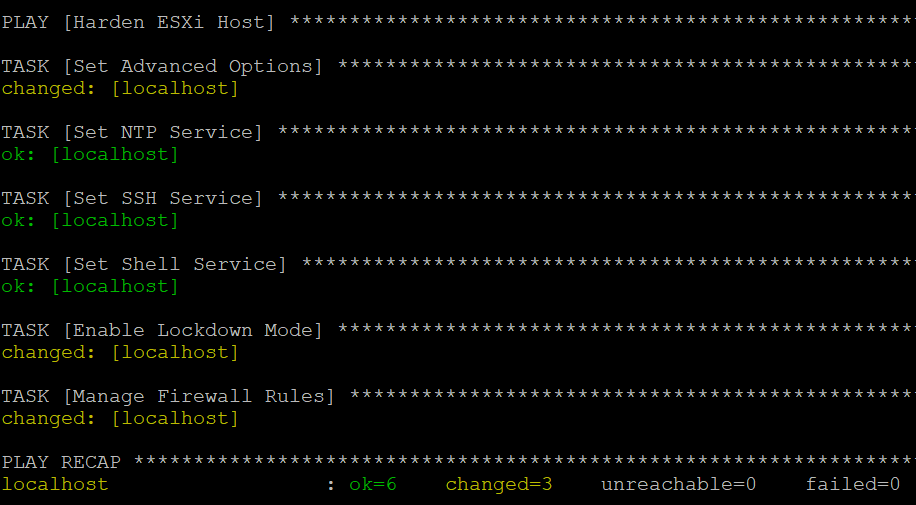
All the above snippets together form my Playbook to enforce the VMware ESXi Security Configuration with Ansible. The Playbook has three debug tasks to identify the required service names, firewall rule names and advanced option keys. The debug tasks can be excluded with the ansible-playbook option –skip-tags debug. If you just want to run the debug tasks without enforcing the security configuration, the ansible-playbook option –tags debug can be used.
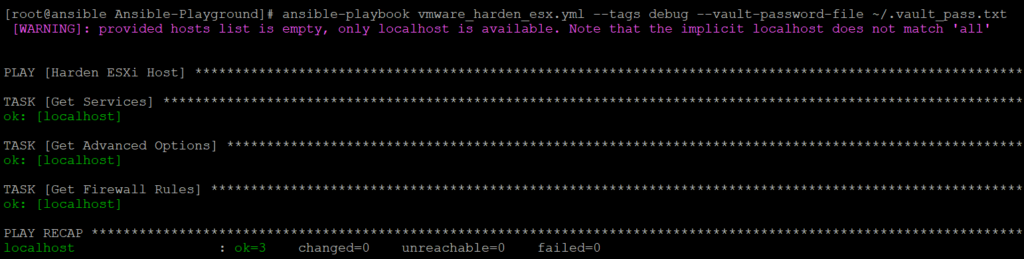
If you additionally add the debug option -vvv, all the debug details (service names, firewall rule names and advanced option keys) will be returned for all hosts in the cluster.
1
|
ansible-playbook vmware_harden_esx.yml --tags debug --vault-password-file ~/.vault_pass.txt -vvv
|
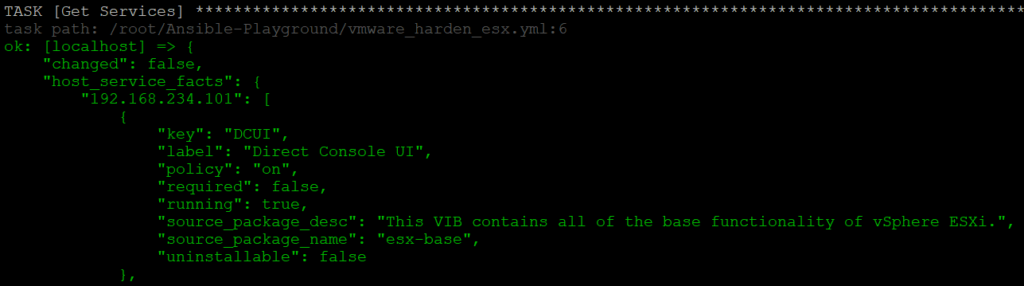
Playbook for ESXi Security Configuration with Ansible
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
|
- name: Harden ESXi Host
gather_facts: no
hosts: localhost
strategy: free
vars:
cluster_name: "cluster01"
tasks:
- name: Get Services
vmware_host_service_facts:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
tags: debug
- name: Get Advanced Options
vmware_host_config_facts:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
tags: debug
- name: Get Firewall Rules
vmware_host_firewall_facts:
hostname: '{{ vcenter_hostname }}'
username: '{{ vcenter_username }}'
password: '{{ vcenter_password }}'
cluster_name: "{{ cluster_name }}"
validate_certs: no
tags: debug
- name: Set Advanced Options
vmware_host_config_manager:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
options:
"UserVars.ESXiShellInteractiveTimeOut": 900
"UserVars.ESXiShellTimeOut": 900
"UserVars.DcuiTimeOut": 600
"UserVars.SuppressShellWarning": 0
"Security.AccountLockFailures": 3
"Security.AccountUnlockTime": 900
"Security.PasswordQualityControl": "similar=deny retry=3 min=disabled,disabled,disabled,disabled,15"
"DCUI.Access": "root"
"Net.BlockGuestBPDU": 1
"Config.HostAgent.plugins.solo.enableMob": false
- name: Set NTP Service
vmware_host_service_manager:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
service_name: ntpd
state: present
service_policy: on
- name: Set SSH Service
vmware_host_service_manager:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
service_name: TSM-SSH
state: absent
service_policy: off
- name: Set Shell Service
vmware_host_service_manager:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
service_name: TSM
state: absent
service_policy: off
- name: Enable Lockdown Mode
vmware_host_lockdown:
hostname: "{{ vcenter_hostname }}"
username: "{{ vcenter_username }}"
password: "{{ vcenter_password }}"
cluster_name: "{{ cluster_name }}"
validate_certs: no
state: present
- name: Manage Firewall Rules
vmware_host_firewall_manager:
hostname: '{{ vcenter_hostname }}'
username: '{{ vcenter_username }}'
password: '{{ vcenter_password }}'
cluster_name: "{{ cluster_name }}"
validate_certs: no
rules:
- name: dhcp
enabled: False
- name: DHCPv6
enabled: False
- name: iSCSI
enabled: False
- name: snmp
enabled: False
|
With Ansible version 2.7.8 the vmware_host_config_manager module is not stable. Under certain conditions, an error occurs:
1
|
The error was: KeyError: 'Vpx.Vpxa.config.log.level'
|
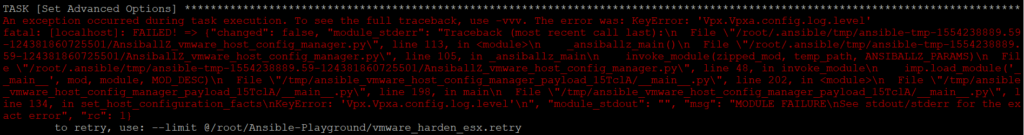
The solution is to use the latest vmware_host_config_manager.py from the Ansible Dev Branch. Related GitHub Issue: Inconsistent results with vmware_host_config_manager
The fix and my whole Ansible Project (in progress) is also available as GitHub repositoy: Ansible-Playground